GCP Pub/Sub Integration Guide
This guide will show you how to integrate Google Cloud Platform (GCP) Pub/Sub with the Secure60 platform. GCP Pub/Sub is a messaging service that allows you to send and receive messages between independent applications. This integration enables you to collect and analyze GCP audit logs and other event data in real-time through Secure60.
Overview
This guide will explain how to configure the Secure60 Collector to pull data from GCP Pub/Sub subscriptions. The integration automatically normalizes GCP event data into the Secure60 Common Information Model (CIM) format, making it easy to analyze and correlate with other security data sources.
Prerequisites
- A GCP project with Pub/Sub enabled
- A GCP service account with Pub/Sub subscription access
- A Secure60 Collector instance (see Secure60 Collector documentation)
- GCP service account credentials JSON file
Configuration Steps
-
Set Up GCP Service Account
- Create a service account in your GCP project
- Grant the service account the following roles:
roles/pubsub.subscriberroles/pubsub.viewer
- Generate and download the service account key (JSON format)
-
Configure Secure60 Collector
Add the following environment variables to your Secure60 Collector
.envfile:GCP_PUBSUB_CREDENTIAL_PATH=/path/to/your/credentials.json GCP_PUBSUB_PROJECT=your-gcp-project-id GCP_PUBSUB_SUBSCRIPTION=your-subscription-idWhere:
GCP_PUBSUB_CREDENTIAL_PATH: Path to your GCP service account credentials JSON file (Details below on how to map this file into the Secure60 Collector container and reference) OR Preferred: Provide an API Key as the valueGCP_PUBSUB_PROJECT: Your GCP project IDGCP_PUBSUB_SUBSCRIPTION: The ID of your Pub/Sub subscription
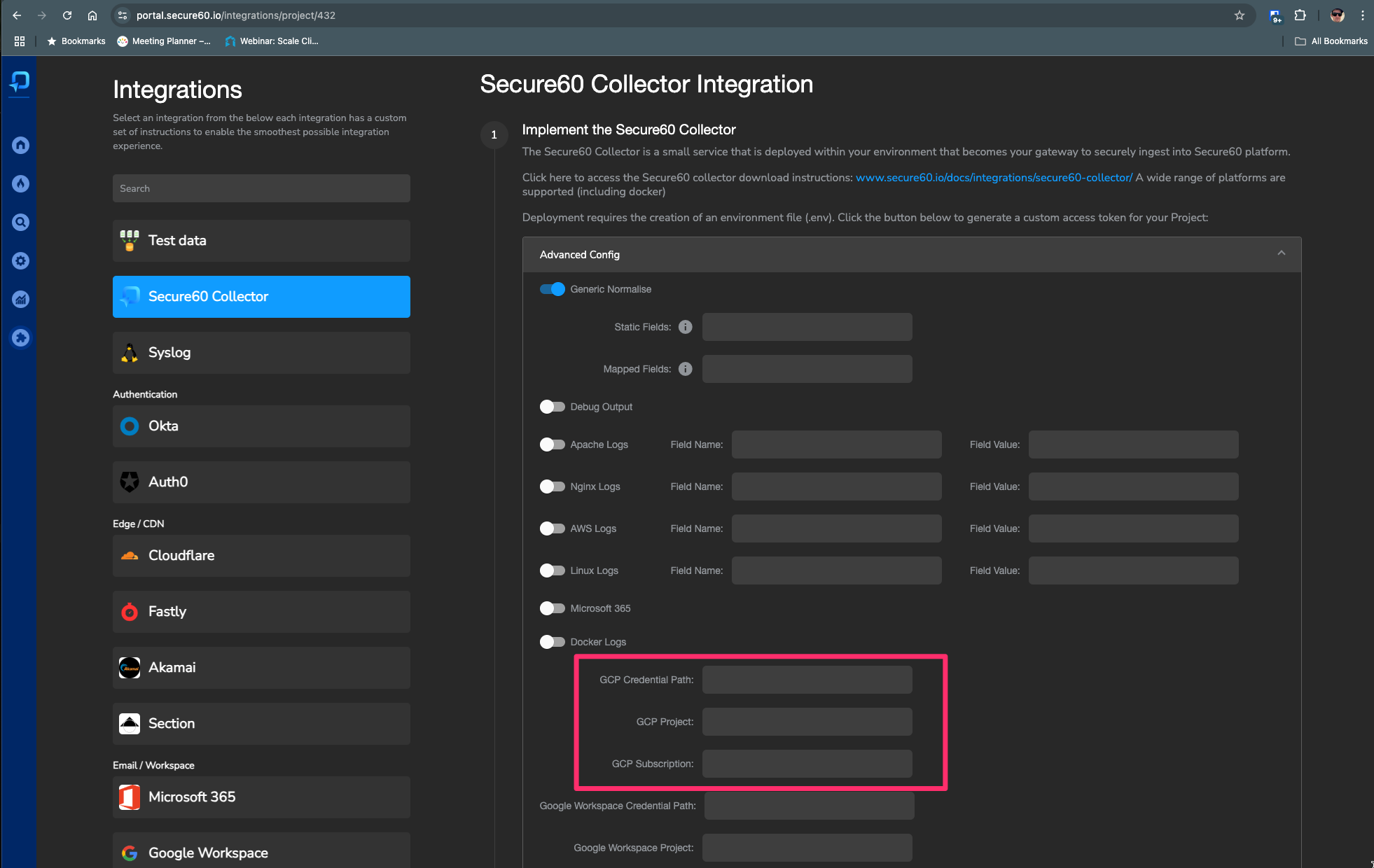
The Secure60 Portal Integrations page provides an intuitive UI to configure GCP Pub/Sub integration. You can enter your GCP Credential Path, Project, and Subscription directly in the portal, which will generate the correct environment variables for your collector deployment.
-
Deploy the Collector
If using Docker, mount the credentials file and update your run command:
docker run -i --name s60-collector \ -v /path/to/your/credentials.json:/etc/vector/gcp-credentials.json \ -p 80:80 -p 443:443 -p 514:514/udp -p 6514:6514 -p 5044:5044 \ --rm -d --env-file .env secure60/s60-collector:1.09Or using Docker Compose:
services: s60-collector: image: "secure60/s60-collector:1.09" volumes: - /path/to/your/credentials.json:/etc/vector/gcp-credentials.json ports: - "443:443" - "80:80" - "514:514/udp" - "6514:6514" - "5044:5044" env_file: - .env
Data Normalization
The Secure60 Collector automatically normalizes GCP Pub/Sub events into the Secure60 Common Information Model. This includes:
- Event timestamps
- User authentication information
- Resource access details
- API operations
- Source and destination information
- Error messages and status codes
Verification
To verify the integration is working:
-
Check the Secure60 Collector logs:
docker logs s60-collector -
View events in the Secure60 Portal:
- Navigate to the Search page
- Filter for events with
vendor="google"andproduct="GPC"
Troubleshooting
Common issues and solutions:
-
Authentication Errors
- Verify the service account credentials file path is correct
- Ensure the service account has the necessary permissions
- Check the credentials file is properly mounted in the container
-
Connection Issues
- Verify the GCP project ID is correct
- Ensure the subscription ID exists and is accessible
- Check network connectivity to GCP services
-
Data Not Appearing
- Verify events are being published to the subscription
- Check the Secure60 Collector logs for any transformation errors
- Ensure the subscription is active and has messages
For additional assistance, contact Secure60 Support at support@secure60.io

Best Practices
- Regularly rotate service account credentials
- Monitor subscription message backlog
- Use appropriate IAM roles and permissions
- Consider using separate subscriptions for different types of events
- Implement proper error handling and retry logic