Windows Server - Integration Guide
This guide will show you how to integrate Windows server (or desktop) into the Secure60 platform using Windows Event Forwarding.
Overview
This guide explains how to configure Windows Event Forwarding to send Windows event logs directly to a Secure60 collector server. This method leverages native Windows functionality and doesn’t require additional agent software. For more information about Windows Event Forwarding, see the Microsoft documentation.
Prerequisites:
- Windows Server with administrative access
- Secure60 collector server with Windows Event Forwarding module enabled
- Network connectivity to the Secure60 collector on port 5986
Setup Process
Step 1: Secure60 Collector Configuration
Before configuring your Windows server, ensure the Secure60 collector has:
- Windows Event Forwarding module enabled
- Port 5986 opened for Windows Event Forwarding traffic
Contact Secure60 Support to enable this module on your collector.
Step 2: Obtain Server Hostname
Run the following command on your Windows server to get the hostname:
hostname
Provide this hostname to the Secure60 team so they can generate the required certificates.
Step 3: Install Certificates
The Secure60 team will provide you with:
- A client certificate for your Windows server
- A CA certificate (for the CA that signed the server certificate)
3.1 Install the Client Certificate:
- Open Certificate Manager (certmgr.msc)
- Navigate to Personal > Certificates
- Right-click on the Personal folder and select All Tasks > Import…
- Follow the Certificate Import Wizard
- Important: Check the box “Include all extended properties” during import
3.2 Install the CA Certificate:
- Open Certificate Manager (certmgr.msc)
- Navigate to Trusted Root Certification Authorities > Certificates
- Right-click on the Trusted Root Certification Authorities folder and select All Tasks > Import…
- Follow the Certificate Import Wizard to install the CA certificate
3.3 Configure Certificate Permissions:
- In Certificate Manager, locate your client certificate in Personal > Certificates
- Right-click on the client certificate and select Manage Private Keys
- Add the Network Service account and grant it Read permissions
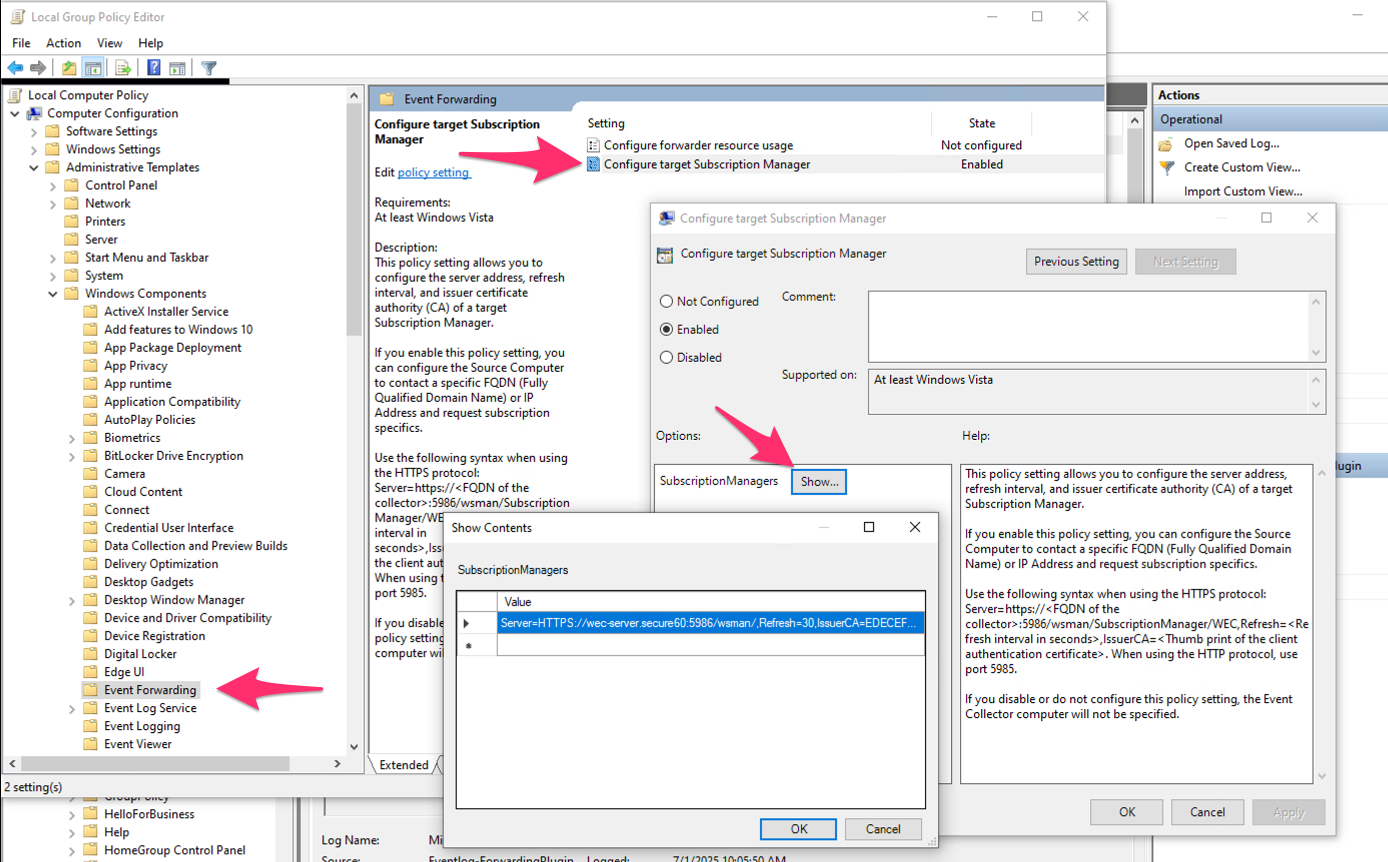
Step 4: Configure Windows Event Forwarding
3.4 Modify Local Policy:
- Open Local Group Policy Editor (gpedit.msc)
- Navigate to: Computer Configuration > Administrative Templates > Windows Components > Event Forwarding
- Double-click on Configure target Subscription Manager
- Select Enabled
- Click Show… next to SubscriptionManagers
- Add the Subscription Manager string provided by Secure60 team
Example configuration:
Server=HTTPS://wec-server.secure60:5986/wsman/,Refresh=30,IssuerCA=<CA_THUMBPRINT>
Example:
Server=HTTPS://wec-server.secure60:5986/wsman/,Refresh=30,IssuerCA=EDECEF179CB4246BD476EA75FE0364A822B64B71
3.5 Configure Hosts File (PoC Only): For proof of concept, add an entry to your Windows hosts file:
- Open Notepad as Administrator
- Open
C:\Windows\System32\drivers\etc\hosts - Add a line:
<COLLECTOR_IP> wec-server.secure60 - Save the file
Note: In production, this would be handled by proper DNS configuration.
3.6 Verify WinRM Service: Ensure the Windows Remote Management service is running:
sc query winrm
If not running, start it:
net start winrm
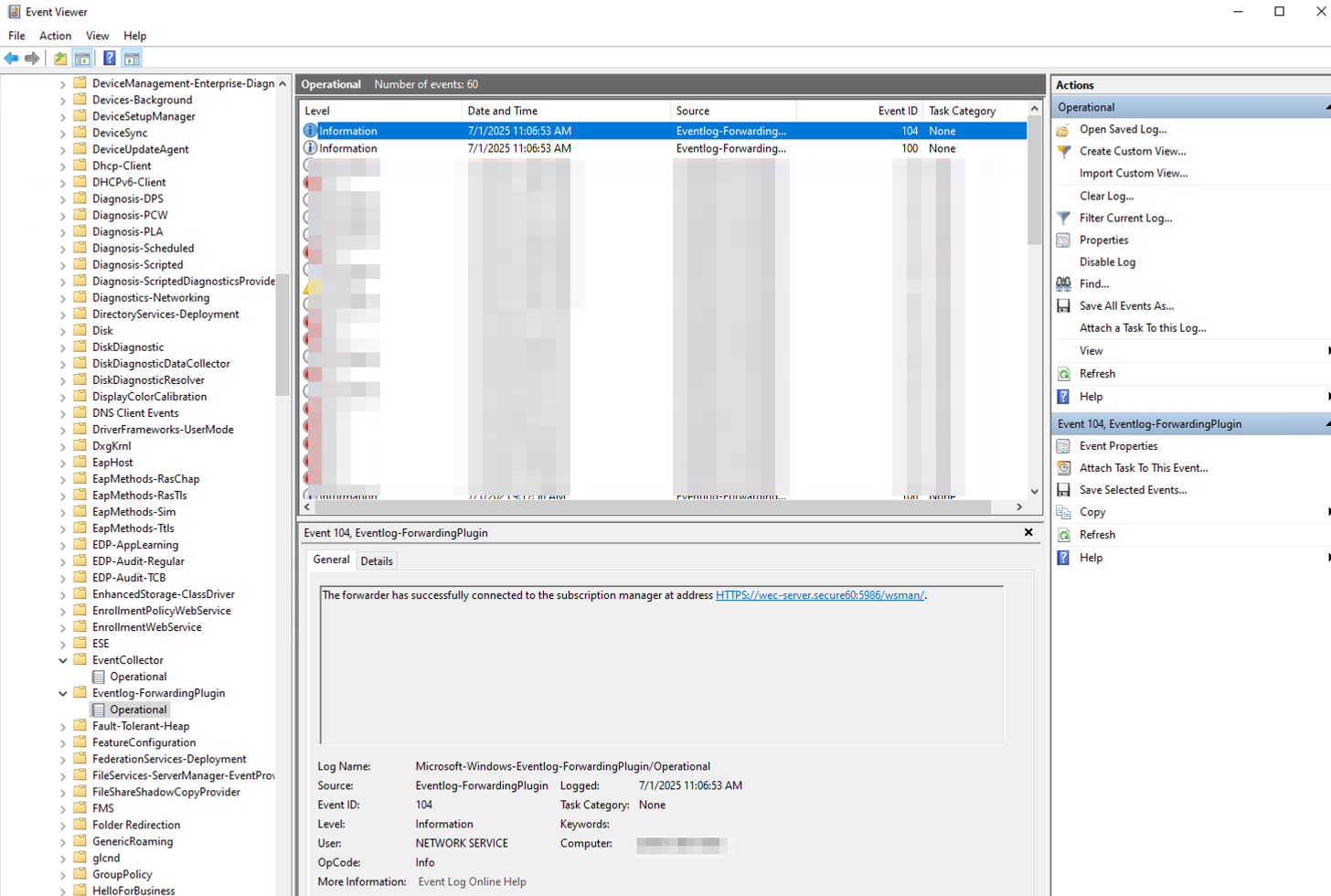
3.7 Check for Errors:
- Open Event Viewer (eventvwr.msc)
- Navigate to Applications and Services Logs > Microsoft > Windows > Eventlog-ForwardingPlugin > Operational
- Look for Event ID 104 (successful connection) or any error events
Verification
After configuration, you should see:
- Event ID 104 in the Eventlog-ForwardingPlugin Operational log indicating successful connection
- Windows events appearing in your Secure60 portal
Troubleshooting
Common Issues:
- Certificate errors: Verify both client and CA certificates are properly installed
- Network connectivity: Ensure port 5986 is accessible to the Secure60 collector
- Permission errors: Verify Network Service has read access to the client certificate private key
- DNS resolution: For PoC, ensure the hosts file entry is correct
Log Locations:
- Windows Event Forwarding logs:
Applications and Services Logs > Microsoft > Windows > Eventlog-ForwardingPlugin > Operational - WinRM logs:
Windows Logs > System(filter by source “Microsoft-Windows-WinRM”)
Support
If you encounter any issues during setup, don’t hesitate to contact Secure60 Support. Please provide:
- Windows server hostname
- Any error messages from Event Viewer
- Certificate installation status