Deployment Manager
Overview
Secure60 offers a standalone Deployment Manager instance to assist in managing configuration at scale. The Deployment Manager is a comprehensive web-based portal that provides centralized control over your Secure60 infrastructure deployment and management operations.
Key capabilities include:
- Configuration Management: Centralized source of truth for 100’s to 1000’s of Secure60 Collector instances
- Automated Deployment: Streamlined rollout of configurations and updates across your environment
- Health Monitoring: Execute health checks on Collectors and system components
- Action Automation: Define and execute custom management tasks and operational procedures
- Inventory Management: Track and organize target servers and deployment groups
- Audit Trail: Complete logging and history of all deployment activities
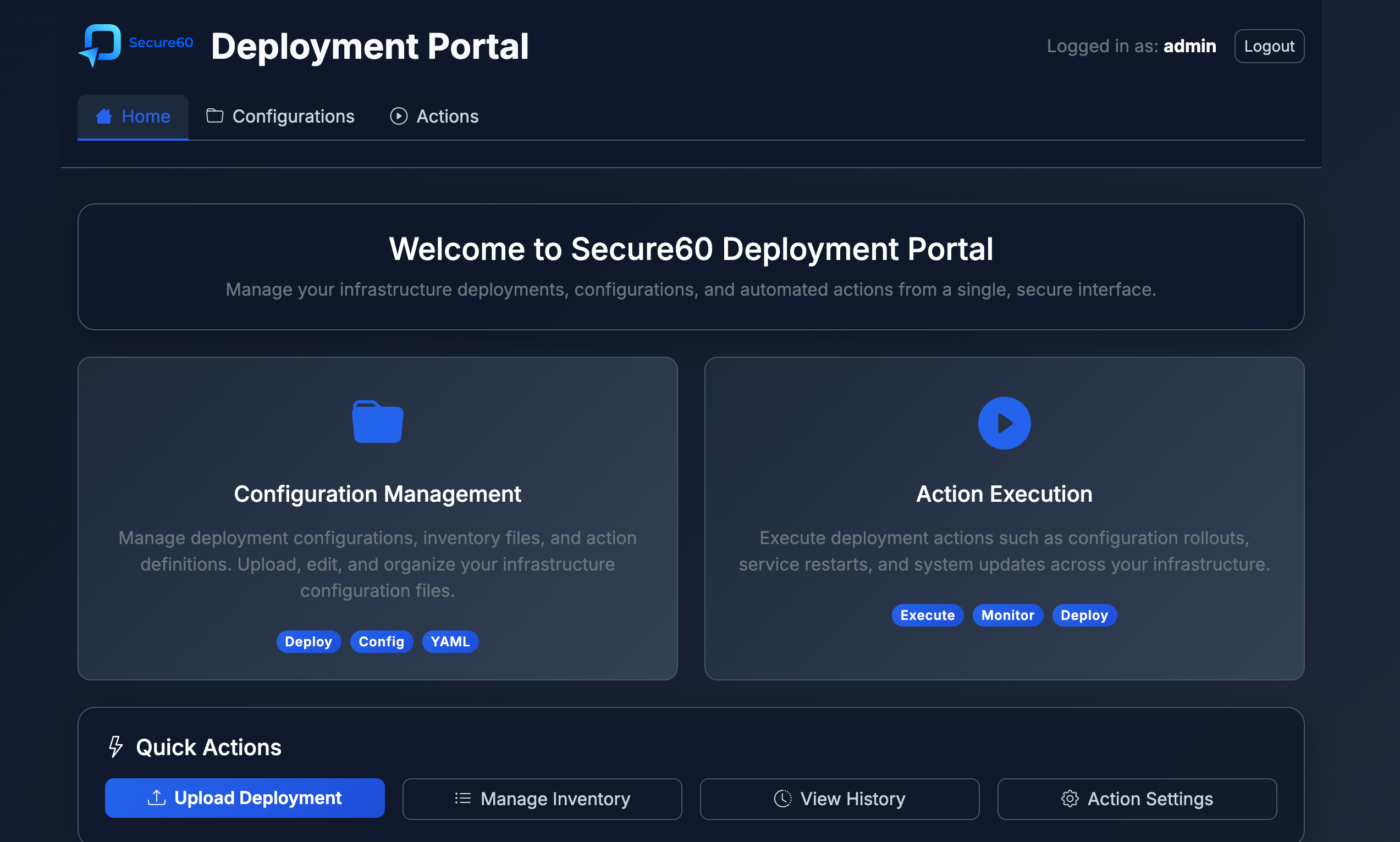
Figure: Deployment Manager web interface showing the modern dashboard with actions management, search functionality, and execution controls
Main Components
The Deployment Manager consists of several integrated components that work together to provide comprehensive infrastructure management:
Web Portal Interface
- Modern Dashboard: Intuitive web interface with dark theme and responsive design
- User Authentication: Secure login system with session management
- Navigation: Organized into Home, Configurations, and Actions sections
Configuration Management System
- Deployments Folder: Store and manage deployment packages and scripts
- Inventory Management: Define target servers and server groups in structured text files
- Version Control: Track changes and maintain configuration history
- File Browser: Web-based interface to browse, edit, and upload configuration files
Actions Engine
- Action Definitions: JSON-based action templates with parameterized inputs
- Script Execution: Execute shell scripts, Ansible playbooks, and custom automation
- Real-time Output: Live streaming of execution output and results
- Execution History: Complete audit trail of all executed actions with parameters and results
Security & Authentication
- User Management: Support for multiple users with individual credentials
- Session Control: Secure session management with configurable timeouts
- Audit Logging: Comprehensive logging of user activities and system operations
- SSH Key Management: Secure storage and management of deployment credentials
Deployment
The Deployment Manager is distributed as a containerized solution for easy deployment and management.
Prerequisites
- Docker and Docker Compose installed on target system
- Network access to target servers for deployment operations
- Adequate storage for configuration files and execution logs
Getting Started
Contact the Secure60 support team for:
- Docker container image access and credentials
- Initial setup and configuration assistance
- Integration guidance for your specific environment
- Training and best practices documentation
The support team will provide:
- Deployment Manager container image
- Sample configuration files and action templates
- Setup documentation and deployment scripts
- Integration assistance for your environment
Usage Workflow
Initial Setup
- Container Deployment: Deploy the Deployment Manager using provided Docker Compose configuration
- User Configuration: Set up user accounts and authentication credentials
- Network Setup: Configure network access to target servers and systems
- SSH Key Setup: Upload and configure SSH keys for passwordless deployments
Configuration Management
- Upload Configurations: Use the web interface to upload deployment packages and configuration files
- Organize Inventory: Create and maintain inventory files defining target server groups
- Define Actions: Create JSON action definitions for common deployment and management tasks
- Test Connectivity: Verify connectivity and access to target systems
Deployment Operations
- Select Action: Choose from available actions (deploy, health-check, update, etc.)
- Configure Parameters: Set deployment targets, configuration options, and execution parameters
- Execute Deployment: Run the action with real-time monitoring of progress and output
- Review Results: Examine execution logs, verify successful deployment, and troubleshoot issues
- Audit Trail: Review execution history and maintain deployment records
Monitoring & Maintenance
- Health Checks: Regular execution of system health verification actions
- Update Management: Coordinate and execute system updates across infrastructure
- Configuration Drift: Monitor and correct configuration inconsistencies
- Performance Monitoring: Track deployment success rates and execution times
Docker Compose File Mapping
The Deployment Manager uses Docker Compose for container orchestration with the following volume mappings:
services:
client-deployment-portal:
build: .
ports:
- "8080:80"
volumes:
- ./deployments:/deployments # Deployment packages and configurations
- ./inventory:/inventory # Server inventory and target definitions
- ./actions:/actions # Action definitions and automation scripts
- ./logs:/logs # Execution logs and audit trails
- ./secrets:/secrets # SSH keys and authentication credentials
environment:
- USER_DATA=admin:s60admin123 # User authentication (comma-separated)
restart: unless-stopped
Volume Details
./deployments:/deployments
- Contains deployment packages, configuration files, and artifacts
- Organized by project, environment, or deployment type
- Supports nested directory structures for complex deployments
- Web interface provides file management capabilities
./inventory:/inventory
- Server inventory files in text format
- Define target servers, groups, and connection parameters
- Support for different environments (production, staging, development)
- Include server hostnames, IP addresses, and SSH port configurations
./actions:/actions
- JSON action definition files
- Custom scripts for deployment, health checks, and maintenance tasks
- Parameterized templates for reusable automation
- Integration points for Ansible, shell scripts, and custom tools
./logs:/logs
- Execution logs and audit trails
- JSON-formatted execution records with timestamps and parameters
- Historical data for compliance and troubleshooting
- Performance metrics and deployment success tracking
./secrets:/secrets
- SSH private keys for passwordless authentication
- Secure credential storage for deployment operations
- Access controlled through container security mechanisms
- Separate from configuration files for enhanced security
Environment Configuration
USER_DATA Environment Variable
- Format:
username:password,username2:password2 - Supports multiple user accounts
- Session-based authentication with configurable timeouts
- Future versions will support LDAP/Active Directory integration
Network Configuration
- Default port mapping:
8080:80(HTTP) - HTTPS configuration available with SSL certificate mounting
- Internal container network for secure operation
- Firewall considerations for target server connectivity