Multi Tenancy
Secure60 provides a robust multi-tenant architecture that supports complex organisational structures, from simple single-organisation deployments to sophisticated enterprise hierarchies with multiple subsidiary organisations. This flexible approach enables organisations to maintain data separation, implement granular access controls, and support diverse business requirements within a unified platform.
Organisational Hierarchy
Overview
Secure60’s organisational structure is built around a hierarchical model that mirrors real-world business relationships. Organisations can have multiple levels of sub-organisations, enabling enterprises to structure their security operations to match their business organisation.
Organisation Layers
The platform supports unlimited levels of organisational depth:
- Root Organisation - The top-level organisation that owns the Secure60 instance
- Sub-Organisations - Child organisations that inherit certain properties from their parent
- Nested Hierarchies - Sub-organisations can have their own sub-organisations, creating deep organisational trees
Key Characteristics
- Inheritance Model - Child organisations can inherit settings, rules, and configurations from parent organisations
- Selective Inheritance - Organisations can choose which elements to inherit and which to customise
- Data Isolation - Each organisation maintains complete data separation unless explicitly shared
- Administrative Boundaries - Clear separation of administrative responsibilities between organisations
Organisational Structure Benefits
Business Alignment
- Mirror Corporate Structure - Align security operations with business organisational charts
- Subsidiary Management - Manage multiple companies or business units within a single platform
- Geographic Divisions - Organise by geographic regions while maintaining centralised oversight
- Functional Separation - Separate organisations by business function or department
Operational Efficiency
- Centralised Management - Manage multiple organisations from a single administrative interface
- Shared Resources - Share threat intelligence, rules, and configurations across organisations
- Scalable Administration - Delegate administrative responsibilities to appropriate organisational levels
- Consistent Policies - Implement consistent security policies across the enterprise
Compliance & Governance
- Data Sovereignty - Ensure data remains within appropriate organisational and geographic boundaries
- Regulatory Compliance - Meet different compliance requirements for different business units
- Audit Separation - Maintain separate audit trails for different organisational entities
- Access Control - Implement fine-grained access controls aligned with business responsibilities
Projects: Data Containers Within Organisations
Project Overview
Within each organisation, data is organised into Projects. Projects serve as logical containers for security data, allowing organisations to segment data based on business requirements, compliance needs, or operational considerations.
Project Characteristics
- Data Isolation - Each project maintains complete data separation
- Independent Configuration - Projects can have unique rules, dashboards, and settings
- Flexible Scope - Projects can represent any logical grouping of data sources
- Access Control - Users can have different permissions across different projects
Common Project Patterns
Geographic Projects
Organisation: Global Corp
├── Project: North America
├── Project: Europe
├── Project: Asia Pacific
└── Project: Latin America
Business Unit Projects
Organisation: Enterprise Inc
├── Project: Finance Department
├── Project: IT Operations
├── Project: Manufacturing
└── Project: Sales & Marketing
Environment Projects
Organisation: Tech Company
├── Project: Production Environment
├── Project: Staging Environment
├── Project: Development Environment
└── Project: Partner Integrations
Compliance Projects
Organisation: Financial Services
├── Project: PCI DSS Scope
├── Project: SOX Compliance
├── Project: General Operations
└── Project: Customer Data
Data Retention Control
Projects control data retention periods, allowing organisations to implement different retention policies based on business needs, compliance requirements, or cost considerations:
- Project-Specific Retention - Each project can have its own data retention period (e.g., 90 days, 1 year, 7 years)
- Compliance Alignment - Set retention periods to meet specific regulatory requirements for different data types
- Cost Optimization - Use shorter retention periods for high-volume, low-value data and longer periods for critical security data
- Automatic Lifecycle Management - Data is automatically archived or deleted based on project retention settings
Retention Examples
Project: PCI DSS Compliance Data → 3 years retention
Project: General Security Logs → 1 year retention
Project: Critical Infrastructure → 7 years retention
Project: Development Environment → 90 days retention
Project Management
- Dynamic Creation - Create projects as business needs evolve
- Data Migration - Move data between projects when organisational structures change
- Project Templates - Use templates to standardise project configuration
- Cross-Project Analytics - Analyse data across multiple projects when appropriate permissions exist
User Management at Organisation Level
User Assignment Model
Users in Secure60 are assigned at the Organisation level, not at the project level. This design provides flexibility while maintaining administrative simplicity.
How User Access Works
Organisation Assignment
- Primary Organisation - Each user is assigned to a primary organisation
- Organisation Hierarchy - Users can access their assigned organisation and any sub-organisations
- Cross-Organisation Access - Users can be granted access to multiple organisations when needed
- Administrative Scope - Administrative privileges apply within the user’s assigned organisational scope
Project Access Control
Once assigned to an organisation, users can be granted specific permissions to projects within that organisation:
- Full Project Access - Complete access to all data and configuration within specific projects
- Read-Only Access - View-only access to specific projects
- Limited Access - Access to specific data types or time ranges within projects
- No Access - Explicit denial of access to sensitive projects
User Role Examples
Organisation Administrator
User: Jane Smith
Organisation: Global Corp (Root)
Access: All sub-organisations and all projects
Permissions: Full administrative access
Regional Security Manager
User: John Doe
Organisation: Global Corp - Europe
Access: Europe organisation and sub-organisations
Permissions: Manage European projects and users
SOC Analyst
User: Alice Johnson
Organisation: Global Corp - North America
Project Access: Production Environment, Staging Environment
Permissions: Read access to security events, create investigations
Compliance Officer
User: Bob Wilson
Organisation: Global Corp (Root)
Project Access: PCI DSS Scope, SOX Compliance (across all regions)
Permissions: Read access to compliance-related data and reports
Inheritance and Configuration
Feature Inheritance Overview
Secure60’s multi-tenant architecture supports comprehensive feature inheritance between organisations, enabling parent organisations to share capabilities, configurations, and resources with their child organisations. This inheritance model promotes consistency, reduces administrative overhead, and ensures standardised security practices across the enterprise.
Inheritable Features
The following features can be inherited from parent to child organizations:
- Rules - Detection rules and correlation logic
- Responses - Automated response actions and workflows
- Reports - Standardized reporting templates and schedules
- Tags - Data classification and labeling schemes
- Tokens - API tokens and integration credentials
- Users - User accounts and role assignments (with appropriate permissions)
Feature Inheritance Flow
The diagram below illustrates how features flow from parent organisations to child organisations, enabling comprehensive inheritance of security capabilities:
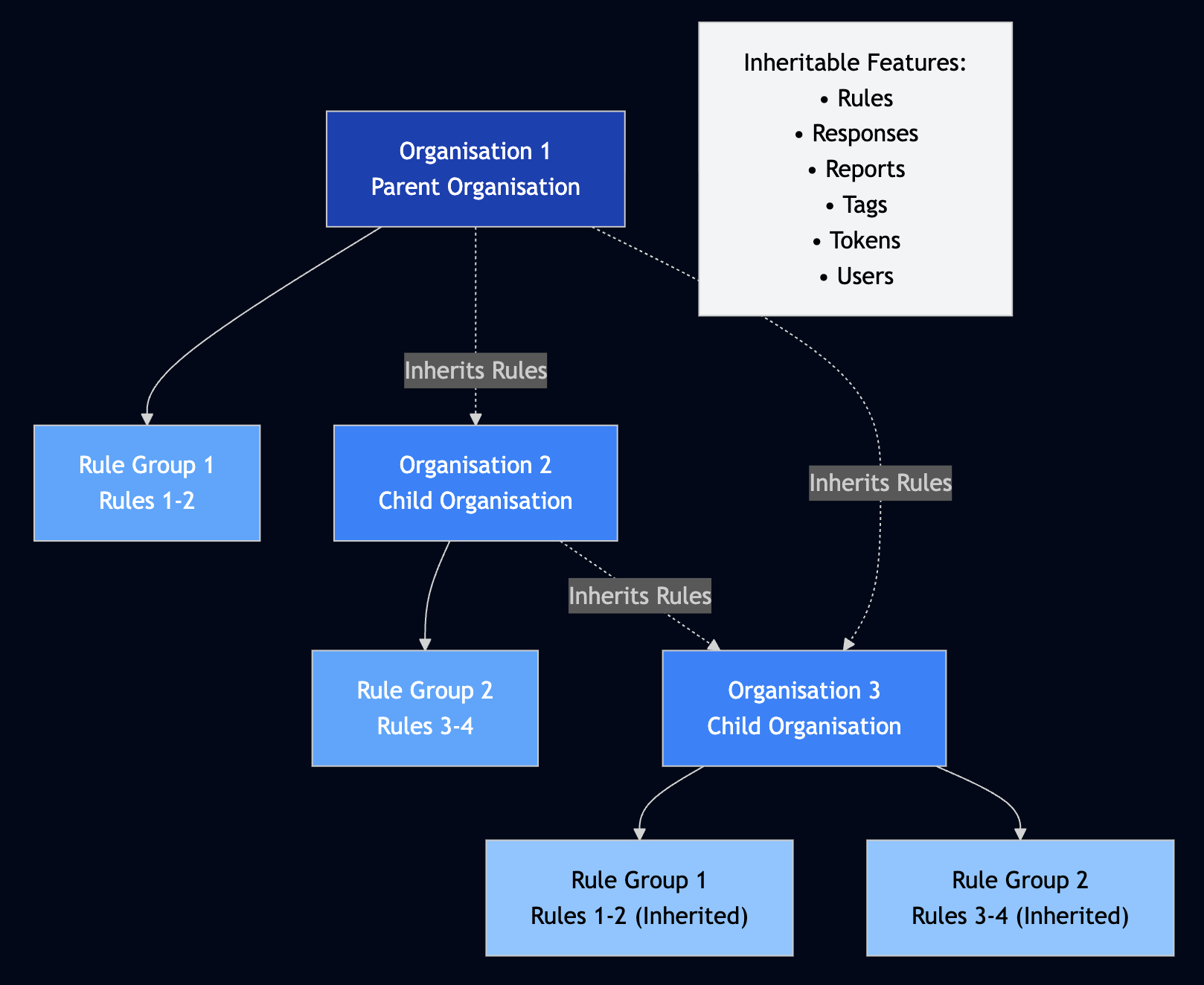
As shown in the inheritance model:
- Parent organisations define and maintain core features (rules, responses, reports, etc.)
- Child organisations automatically inherit these features while retaining the ability to customise
- Nested inheritance allows features to flow through multiple organisational levels
- Selective inheritance enables organisations to choose which features to inherit or override
Configuration Inheritance
Sub-organisations can inherit various configuration elements from their parent organisations:
Inheritable Elements
- Detection Rules - Share threat detection rules across the organisation
- Threat Intelligence - Distribute threat intelligence feeds to all sub-organisations
- Data Classification - Apply consistent data classification schemes
- Retention Policies - Implement standardised data retention across the enterprise
- Integration Configurations - Share common integration settings
Customisation Options
- Override Inheritance - Sub-organisations can override inherited settings when needed
- Additive Configuration - Add organisation-specific settings alongside inherited ones
- Selective Inheritance - Choose which elements to inherit from parent organisations
- Local Customisation - Implement organisation-specific configurations for unique requirements
Feature Inheritance Examples
Rule Inheritance
Parent Organisation: Global Security Baseline
├── Rule Group: Failed Authentication Detection
├── Rule Group: Malware Detection
└── Rule Group: Data Exfiltration Detection
Child Organisation: European Division
├── Inherits: All parent rule groups
├── Adds: GDPR-specific data access rules
└── Customises: Adjusted thresholds for regional patterns
Response Inheritance
Parent Organisation: Standard Incident Response
├── Email Notifications → Security Team
├── Ticket Creation → ITSM System
└── Automated Blocking → Firewall
Child Organisation: Finance Division
├── Inherits: All parent responses
├── Adds: Regulatory notification → Compliance Team
└── Enhances: Priority escalation for financial systems
Report Inheritance
Parent Organisation: Executive Reporting Suite
├── Monthly Security Dashboard
├── Compliance Summary Report
└── Threat Intelligence Briefing
Child Organisations: All Subsidiaries
├── Inherit: All parent reports with organisation-specific data
├── Customise: Branding and contact information
└── Extend: Additional local compliance reports
Data Retention Control
Parent Policy: Standard 7-year retention
├── Financial Sub-Org: 10 years (regulatory requirement)
├── Development Sub-Org: 1 year (cost optimization)
├── PCI Environment: 3 years (PCI DSS compliance)
└── General Operations: 7 years (inherited policy)
Multi-Tenant Security
Feature Inheritance Benefits
The comprehensive feature inheritance model provides significant operational and security advantages:
Operational Efficiency
- Centralised Management - Define security policies once at the parent level and automatically distribute to child organisations
- Consistent Security Posture - Ensure all organisations benefit from the latest threat detection capabilities
- Reduced Administrative Overhead - Minimise duplication of effort across multiple organisations
- Rapid Deployment - New security features automatically available to all child organisations
Flexibility and Control
- Selective Inheritance - Choose which features to inherit and which to customise locally
- Override Capability - Child organisations can override inherited features when business needs require it
- Additive Configuration - Add organisation-specific features alongside inherited ones
- Version Control - Track changes to inherited features across the organisational hierarchy
Data Isolation
- Complete Separation - Each organisation’s data is completely isolated from others
- Encrypted Storage - All data encrypted with organisation-specific keys
- Network Isolation - Logical network separation between organisational data flows
- Access Logging - Complete audit trail of all cross-organisational access
Administrative Separation
- Role-Based Boundaries - Administrative roles respect organisational boundaries
- Audit Independence - Each organisation maintains independent audit logs
- Configuration Isolation - Organisation configurations cannot interfere with each other
- Backup Separation - Data backups maintain organisational separation
Implementation Best Practices
Planning Your Organisational Structure
- Map Business Structure - Align security organisation with business organisation
- Consider Compliance - Factor in regulatory requirements for different business units
- Plan for Growth - Design structure to accommodate future organisational changes
- Define Data Flows - Understand how data should flow between organisations
User Management Strategy
- Principle of Least Privilege - Grant minimum necessary access to each user
- Regular Access Reviews - Periodically review user access across organisations
- Role Standardisation - Develop standard roles that can be applied across organisations
- Onboarding/Offboarding - Establish clear processes for user lifecycle management
Feature Inheritance Strategy
- Inheritance Planning - Design which features should be inherited vs. customised at each organisational level
- Version Management - Establish processes for updating inherited features across the organisation
- Override Governance - Define clear policies for when child organisations can override inherited features
- Change Communication - Implement communication processes for feature updates that affect multiple organisations
Project Organisation
- Logical Grouping - Group related data sources into coherent projects
- Clear Boundaries - Ensure project boundaries align with business and compliance needs
- Retention Planning - Design project retention policies to balance compliance, cost, and operational needs
- Consistent Naming - Use consistent naming conventions across organisations
- Documentation - Maintain clear documentation of project purposes, scope, and retention requirements
Getting Started with Multi-Tenancy
Initial Setup
- Design Organisation Structure - Plan your organisational hierarchy
- Create Organisations - Set up parent and child organisations
- Configure Inheritance - Set up appropriate inheritance relationships
- Create Projects - Establish initial projects within organisations
- Assign Users - Add users to appropriate organisations with correct permissions
Migration Considerations
- Existing Deployments - Migrate existing single-tenant deployments to multi-tenant structure
- Data Migration - Plan for moving existing data into appropriate projects
- User Transition - Transition existing users to new organisational structure
- Configuration Updates - Update existing configurations to work with new structure
For detailed implementation guidance and step-by-step setup instructions, visit our Guides section.